AD Security Optimization and Hardening White Paper-04
2024-04-19 20:36:49
3.11 Optimize Patch Update System
The patch optimization of the whole network is an important part of the domain security optimization, and can be said to be the most basic and important part. It is recommended to implement the whole network patch optimization through Microsoft's WSUS.
3.11.1 Overall Architecture of WSUS Patch Server
Considering various factors such as management, dedicated line bandwidth, patch disk occupancy, and access load, the design is as follows:
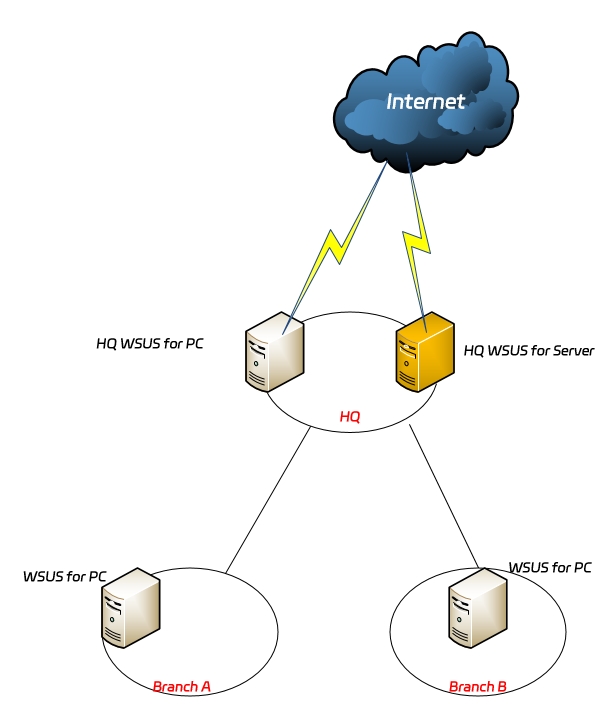
Deploy two WSUS servers at the headquarters, one dedicated to Windows server patches and the other to client operating system patches, to reduce disk occupancy and concurrent access pressure.
The server-specific WSUS at the headquarters is for the servers at the headquarters and branches, and the client-specific WSUS at the headquarters is for the clients at the headquarters.
Branches also deploy a client-specific WSUS server as a subordinate server of the client-specific WSUS server at the headquarters, accepting unified management. The clients at the branches get patch updates from this server.
3.11.2 Hardening of WSUS Patch Server Itself
1, The WSUS patch server is an independent network segment (/30 mask), with the gateway configured in the data center hardware firewall, so that the traffic in and out of the patch server is filtered through the protection of IPS.
Inbound policy only allows access to port 8530 and denies access to any other ports.
The outbound policy is to only allow the patch server to actively visit the Microsoft update server https protocol and the internal network DNS protocol.
2, The patch server can update patches from itself, MU, other WSUS, pay attention to policy configuration, and automatically download and apply the latest patches.
3.11.3 Domain Group Policy for Patch Update
The computers that join the domain can automatically get the patch server address, update time and other parameters through group policy. Computers that do not join the domain can point to the patch server by importing a registry.
When configuring the patch server protocol, use the HTTPS encryption protocol to prevent attackers from intercepting the HTTP protocol on the network and delivering malicious updates.
Considering the network pressure, the patch update time can be set at noon.
Server Patch Update Policy
Servers can be divided into several categories, such as automatic download and manual patch, automatic download and automatic patch.
For domain controllers, it is recommended to automatically download and manually patch. After the latest patch is released, the third DC at the headquarters can immediately update the patch. If there is no problem, other servers can be updated two weeks later.
For the WSUS server itself, patches can be updated as soon as possible.
For other important servers, they can also be handled in this way.
For general servers, edge applications, automatic download and automatic patching can be done.
Client Patch Update Policy
The patches for clients need to be updated on a large scale after a large amount of testing to prevent widespread compatibility issues caused by new patches.
The patch administrator checks whether the latest patch metadata has been synchronized to the primary patch server on the second Wednesday of each month.
Only approve security updates and critical updates for patches.
Manually approve the download of patches and distribute them to the test group computers on the third Wednesday of the week.
If there are no problems with the test group computers, other clients can be approved to install patches on the fourth Wednesday of the week.
3.11.4 Other Notes on Patch Management
Do not use third-party tools to update patches, but third-party tools can be used to check for patch omissions.
The patch administrator should pay attention to hot security information on the Internet, check for patch vulnerabilities, and temporarily import security patches.
Check the patch update report within a week after the patch update, check the patch update failure rate, and notify the desktop operations staff to handle it.
Every quarter, the patch administrator clears expired patches and checks whether the space on the disk where the patches are located is sufficient.
3.12 Use Third-Party Backup Software to Backup AD
First, enable the AD recycle bin to recover recently deleted objects.
Secondly, regular backups of the domain server should also be carried out to achieve disaster recovery in extreme cases. It is recommended to backup centrally through the existing third-party backup platform, because the built-in system backup may be infected or deleted by viruses.
Regularly perform unauthorized restore recovery tests on different machines in the third-party backup platform's AD backup to verify the validity of the AD backup.
Enhance the security protection and reinforcement of the backup system to prevent the backup system from being destroyed at the same time and losing the last straw.
3.13 Treatment of Old Systems in the Domain
For example, client systems before win7, server systems before win server 2008R2, these systems have a large number of security vulnerabilities, and Microsoft no longer provides security patches, the existence of these systems is a great security risk, they are the springboard for hackers to further attack, so those that should be eliminated will be eliminated, those that should be upgraded will be upgraded.
3.14 Build Server Standardization Template
Now most servers are virtual machines, it is recommended to create relevant templates in the virtual machine, and do a good job of basic security reinforcement:
1 The operating system of the template is recommended to use windows server 2019/2022, the lowest cannot be lower than windows server 2012 r2 (support expires on 2023.10.10), cannot use win2008R2 or lower versions, because these versions Microsoft has stopped patch updates, the threat of vulnerabilities is serious, if patches are indeed needed, you can purchase genuine extended licenses.
2 The operating system template must be standardized, do not install unnecessary software, one more software is one more vulnerability point, patch up the latest patches before packaging, if not added to the domain, please enable the following configuration, if added to the domain, it will be implemented uniformly through domain group policy:
l Update to the latest patch l Turn on the system firewall, disable all inbound access, and later open the corresponding ports according to needs (qualified companies recommend that this be achieved through a hardware firewall). l Install anti-virus software, set exit and uninstall passwords, and add exclusions. l Block access to the Internet (manage devices through online behavior) |
l Turn on security audit l Enable locking strategy, such as 5 incorrect locks, lock for 3 minutes, and unlock for 3 minutes. l Modify the Windows security log size. By default, only 2M logs are retained. |
l Disable the server service. If the server service cannot be disabled, at least disable C$ and management shares. l Disable Print Spooler service. l Disable WINRM service. |
l Remote Desktop Services disables client disk mapping and enables clipboard text pasting. l The remote desktop automatically logs out after 2 hours of inactivity. l The remote desktop automatically logs off after 2 hours of disconnection. |
l Disable password caching, or keep a one-time password cache l Disable network credential caching l Conditionally prohibit browsers from saving passwords (IE/EDGE/CHROME) |
l Deny local administrator access to this computer over the network l Clear the AD admins group from the local administrators group |
l Reading of removable media such as USB flash drives is prohibited l Turn off autoplay (all drives) l Do not disable UAC |
3.15 Establish a Standardized Client System
The standardized client system not only makes the terminal computer more stable and reduces the maintenance volume of the administrator, but also is an important part of ensuring the security of the entire network.
Regarding client standardization, the following suggestions are made:
1. Ensure the cleanliness of the source installation medium, and do not use the so-called customized and pure version of the system installed on the Internet. This so-called pure version usually has trojans or malicious software in it, which is like inviting a wolf into the house.
2. In the IT planning of the enterprise, it is recommended to use the latest Win10 enterprise long-term service version, which is more suitable for enterprise use, because Microsoft has a longer support period and the system is relatively streamlined.
3. It is possible to make and deploy an operating system suitable for enterprise standardization (update the latest security patches, and install free general software and purchased genuine software in the template) through Microsoft SCCM and other terminal management platforms, achieving a one-stop system installation, driver installation, domain addition, and terminal security standard configuration.
4. Do not arbitrarily give terminal users administrator privileges. For some special software that requires administrator privileges, it can be implemented through group policy or privilege management software.
Privilege management software can define a whitelist, and the software in this whitelist runs in the system identity, which is simpler than adjusting permissions through group policy.
3.16 Strengthen AD Integrated Security Management
Now there are more and more applications integrated with AD. From a security perspective, the main focus is on:
1. The integrated account is dedicated, only the minimum permissions are granted, do not arbitrarily give domain control administrator or domain administrator permissions, usually a normal domain account is enough, and the password is more than 20 digits, if conditions permit, modify regularly.
2. The authentication process must be encrypted, like LDAP simple authentication, the password is plaintext, easy to be sniffed.
3.17 Build an Early Warning System
An early warning system must be established in order to promptly remind administrators when the domain controller is under attack.
The source of early warning data is network traffic and event logs. Network traffic is often detected and alarmed by the situational awareness system within the enterprise. The domain itself provides rich audit logs, and corresponding alarms are implemented in conjunction with third-party log platforms.
Microsoft's Advanced Threat Analytics (ATA) can alert from both network traffic and logs. ATA is a very good domain security threat perception platform, highly recommended.
Domain audit logs need to enable audit policies, which include traditional and advanced parts. Advanced auditing needs to be enabled, and traditional auditing can no longer meet the needs of early warning.
Since audit logs are scattered on each DC and are poorly readable and have limited capacity, it is recommended to implement centralized storage, retrieval, and alert of logs through centralized log audit equipment.
The following are important logs suggested to be monitored and alerted, especially those marked as "Potential Severity" are high, which must be monitored.
Current Windows event ID | Legacy Windows event ID | potential severity | event summary |
4618 | null value | high | A monitored security event pattern has occurred. |
4649 | not applicable | high | Replay attack detected. Possibly a harmless false positive due to a configuration error. |
4719 | 612 | high | System audit policy has changed. |
4765 | null value | high | SID history added to account. |
4766 | null value | high | An attempt to add SID history to the account failed. |
4 769 | null value | high | Kerberoasting |
4794 | null value | high | Try setting directory services restore mode. |
4897 | 801 | high | Role separation enabled: |
4964 | null value | high | A special group has been assigned to the new login. |
5124 | null value | high | Updated security settings on OCSP responder service |
null value | 550 | medium to high | Possible Denial of Service (DoS) Attack |
1102 | 517 | medium to high | Audit log cleared |
