AD Security Optimization and Hardening White Paper-05
2024-04-19 20:51:20
Chapter 4 Technical-Tactical Level Optimization and Reinforcement Measures
Under the requirements of the previous management level and technical strategic level, this section will discuss more detailed and targeted optimization and reinforcement measures at the tactical level.
4.1 Domain Control Reinforcement
4.1.1 Check and Clean-up Work
4.1.1.1 Check and Clean-up of Old Objects
The existence of old objects is an important risk factor for the domain. Relevant checks and clean-ups mainly include:
Abandoned account and inactive account cleaning
First of all, it is necessary to clean up abandoned or expired objects. The existence of these expired accounts is a potential threat to the entire domain environment. The more accounts there are, the larger the attack surface for password cracking and password spraying, and the higher the probability that an account will be successfully cracked. The first step for hackers to break the domain control is usually to get the password information of a normal domain account. Since old accounts are not used, even if they are locked during a brute force attack, they are difficult to be discovered and are more likely to facilitate a successful attack.
Cleaning up thinking: Set up a temporary OU, such as <Resources being cleaned>, and move the users and computers of the following time period to it.
Users: Users who have not logged in for half a year, but exclude some special accounts.
Computers: Computers that have not logged in for half a year.
Operation: First disable, and then delete after three months.
The remaining users, computers, and servers should be placed under the corresponding organizational units.
Other resources to be cleaned: Useless organizational units and group policy objects.
Empty password accounts, password never expires accounts check and clean up
DES encryption accounts, SID history accounts check and clean up
4.1.1.2 Other abnormal checks and treatments
Including but not limited to the following items:
1 Whether there is a sniffer sniffing tool installed on the DC
2 Check the members of the "PRE-WINDOWS 2000 COMPATIBLE ACCESS" group, it should be empty.
3 Whether any DNS zone is configured as non-secure update, it should be a secure update.
4 Whether there is a dedicated password policy for service accounts (more than 20 digits)
5 Whether there is a GPO that disables LLMNR and WPAD (should be disabled)
6 Whether there are group policy preference passwords saved in the GPO.
7 Duplicate SPN check
8 Master key attack check
9 Whether there is a certificate template that allows the requester to specify the subjectAltName.
4.1.2 Privilege Check and Reinforcement
4.1.2.1 Built-in Administrator Group Strengthening

- For overall protection measures for the default domain administrator, EA group, DA group, BA group, and client local administrators group, refer to the above figure.
- Clear all members except the administrator from the domain local administrators group. The administrator can only log in to the domain control locally and is generally not used. Add a new dcadmin, join the BA group, bind to the domain control, and can't log in to others. It is recommended that dcadmin be controlled by an administrator, and it completes relevant high-level tasks because other management tasks can be completed by site administrators. This way, there is no need to create multiple BA group members.
- Delete all users from the Domain admins, Enterprise Admins, and Schema admins. Create a new rootadmin for backup, and only add it to the DA/EA/SA group when in use.
To prevent forgetting to clear, use the restricted group function for extra security.
- Clear users in the account operators, backup operators, remote desktop users, server operators, and print operators groups on the domain control.
- Use the Protected Users group to protect administrators.
Users in the Protected Users group will not cache user credentials (so service and computer accounts should not be members of this group). You can put rootadmin in this group. This group also has some side effects, so don't put all privileged accounts in it all at once. The main restrictions are:
If the domain functional level is Windows Server 2012 R2, then the members of the group:
Cannot use NTLM for authentication (for example, direct connections through non-domain computers or direct IP connections cannot be authenticated)
Cannot use the Data Encryption Standard (DES) or RC4 cipher suites in Kerberos pre-authentication
Cannot delegate using unconstrained or constrained delegation
Cannot renew user ticket (TGT) beyond the initial 4-hour lifespan
- Empty the Allowed RODC Password Replication Group group. Each site should create a separate group that needs to cache passwords, rather than putting all the users and computers of all sites in this group.
4.1.2.2 Administrator Strengthening
Including but not limited to:
1 Check whether the administrator account has configured SPN (should not be configured)
2 Whether there are inactive administrator accounts (if so, delete or disable)
3 Whether the administrator is marked as "This account is sensitive and cannot be delegated" (should be marked)
4 Check whether the service account is a domain administrator (should not be a domain administrator)
5 Administrators can be named in Chinese, which may increase the difficulty of attack
4.1.2.3 Other Privilege Checks
1 Check whether there are irregular explicit delegations on the DNS server
2 DSRM backdoor check
If there is DsrmAdminLogonBehavior under the registry HKLM\System\CurrentControlSet\Control\Lsa, and the value is 2, it is likely to be "black".
3 Users with DCSync permissions check
The so-called DCSync permissions generally refer to the following two permissions:
Replicating Directory Changes
Replicating Directory Changes All
This feature is often used by hackers to mimic a domain controller to request data from the real domain controller, such as a user's hash. The biggest feature of this function is that it can obtain data on the domain control without logging into the domain control.
In order to maintain attack permissions, hackers often add a regular user with DCSync permissions for subsequent covert attacks. So it is necessary to check whether the DCSync permission of the domain is owned by a special account.
4 AdminSDHolder Object ACL Check
AdminSDHolder ensures that the permissions of the protected privilege group remain consistent. You need to check the permissions of this object itself to see if there are special users with control permissions.
The list below shows the security groups protected by AdminSDHolder.
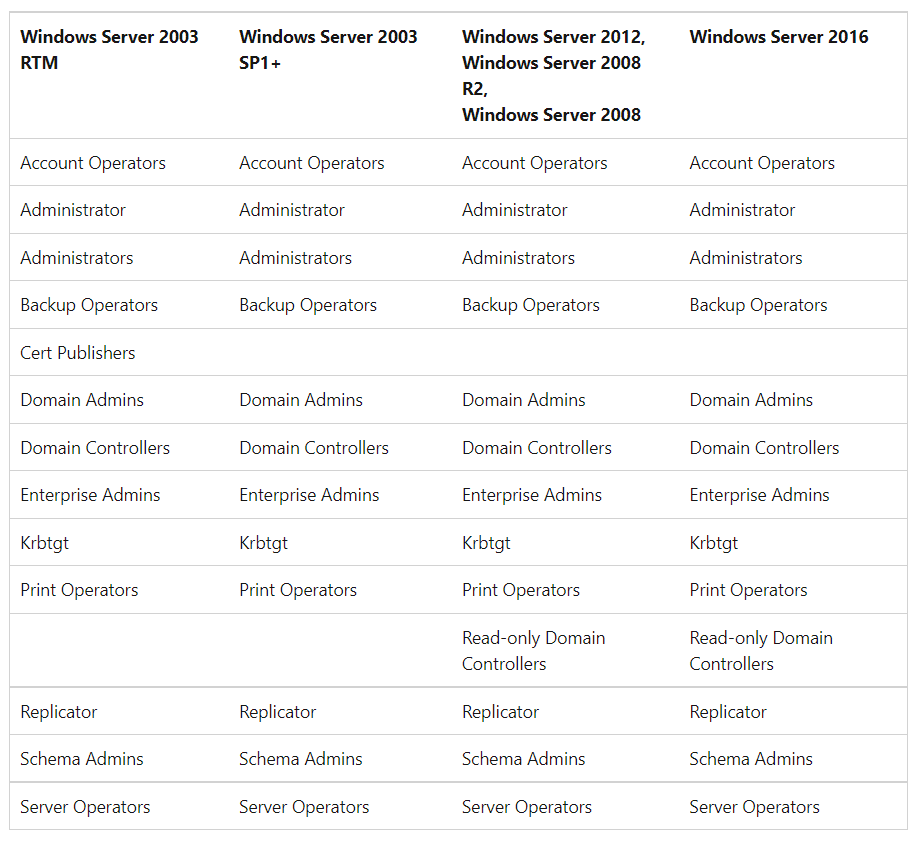
5 Clear the default "Add workstation to domain" authorization
By default, all domain users have the right to add 10 computers to the domain, which is a big exploit point for attackers. This permission needs to be revoked and the authorization cleared. In actual use, domain addition authorizations are made at the OU level, with no limit on the number of additions, which is more suitable for the production environment.
4.1.3 Optimize Network Location
From the perspective of dividing the network into domains for implementing access control, it is always a good idea to put the domain controller in an independent VLAN, and bind static ARP table entries to the domain controller in the core switch, which can prevent the domain controller from being ARP spoofed.
4.1.4 Encrypt Network Communication to Domain Controller
For some applications integrated with AD, such as third-party applications submitting usernames and passwords to AD for authentication, the password may be plaintext and unencrypted in the process from the user to the third-party application, and from the third-party application to the domain controller. For example, if OA integrates with AD, and OA is accessed via HTTP, then the user's submitted username and password are plaintext. In this case, the password has the possibility of being sniffed, so it is recommended that the communication to the domain controller, especially when it comes to identity authentication, must be encrypted, such as using LDAPS, or replacing HTTP with HTTPS.
4.1.5 Domain Controller Patch
Manually check whether the domain controller has updated high-risk patches such as ms14-068, ms17-010, CVE-2019-1040, CVE-2020-1472, CVE-2020-17049, CVE-2021-1675, CVE-2021-34527, CVE-2021-42287, CVE-2021-42278, CVE-2022-20963, etc., and update the patches to the latest version to avoid being directly attacked by known CVE vulnerabilities.
4.1.6 Other Reinforcements
In addition to the general server reinforcement described in section 3.14, DC can also enable LSA protection, disable SMBv1, disable Print Spooler service, stop the domain controller's C$, ADMIN$ management share, and use the hardware firewall's IPS protection.
4.2 General Server Reinforcement
The general reinforcement measures for the server can refer to the description in section 3.14, as well as the following points:
- Remove domain admins from the server's local administrators group, and add dedicated administrator accounts.
- Implement LAPS local administrator password management.
4.3 General Client Reinforcement
Although the most important part of domain security optimization is the security optimization and reinforcement of the domain controller itself,
But we should not ignore the other parts of the domain. The great wall, destroyed by an ant hole, every workstation in the domain should not be ignored. Many cases show that the domain controller is attacked by using a workstation in the internal network as a springboard.
In addition to the measures already described, it is also recommended:
1 It is recommended to disable the server service on the client. If there is a shared printer, you can configure the group policy to open the server service separately.
2 Disable WINRM service
3 Group policy removes the domain admins group from the local administrators group.
4 Group policy adds the site client administrators group to the client administrators group for easy operation and maintenance (disable this group's network share access to prevent virus spread).
5 Deny access to this computer from the network: local administrators group, site client administrators group, domain administrators group.
6 Deploy a client network access control system, only allow computers that join the domain to access the network, this method is transparent and imperceptible to users.
7 Prohibit browser password saving
8 Prohibit automatic playback of USB drives or other devices
9 Do not disable UAC
10 Turn on the system firewall,
11 LAPS local administrator password scheme can be implemented.
Previous: AD Security Optimization and Hardening White Paper-04
Next: No More
